Cybersec (04 handout 1 and 2 Security systems engineering )
It is the statement of responsible decision makers about the protection mechanism of a company's crucial, physical, and information assets.
Security Policy
Policy Makers
Board
Policy Guide
Does not specify a technological solution. Instead, it specifies sets of intentions and conditions that will aid in protecting assets along with its proficiency to organize a business.
Security Policy
Board
Policy Makers
Policy Guide
Security policy development is a joint or collective operation of all entity of an organization that is affected by its rules.
Policy Makers
Security Policy
Board
Policy Guide
(Find right ans) During policy creating, the following entities should be involved in its development:
Board
IT Team
Legal Team
HR Team
Members must render their advice to some form of a review of policies in response to the exceptional or abominable running condition of the business.
Board
IT Team
Legal Team
HR Team
Members of this team usually are the biggest consumers of the policy information in any company because they develop standards around the usage of the computer system, especially security controls.
IT Team
Board
Legal Team
HR Team
This team ensures the legal points in the document and guides a particular point of appropriateness in the company.
IT Team
Board
Legal Team
HR Team
This team typically obtains a certified certificate from each employee, in which they have read and understood the stipulated policy, as it deals with reward- and punishment-related issues of employees to implement discipline.
IT Team
HR Team
Legal Team
Board
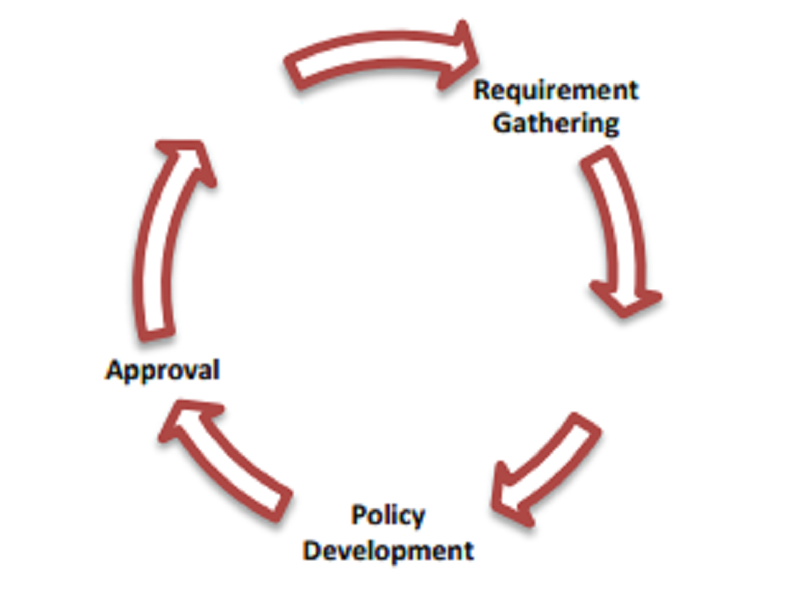
Fill the blank!
Publication and Proposal Definition
Policy Audience and Proposal
Policy Audience and Proposal Definition
Publication and Proposal
Security policy applies to all senior management, employees, stockholders, consultants, and service providers who use company assets. erefore, the security policy must be readable, concise, and illustrated to be effectively understandable to its audience so that everyone adheres to the policies and fulfill their role.
Policy Audience
Policy Guide
Policy Makers
Policy Security
(Find wrong ans) Policy Classification, Every organization typically has three (3) policies:
It is drafted on paper
Is in employees' minds
It is implemented
Is in the bag
It mandates what protection should be wielded to safeguard the physical asset from both employees and management and applies to the prevail facilities, including doors, entry point, surveillance, and alarm.
Physical security
Personnel Management
Hardware and Software
Policy Classification
They are supposed to tell their employees how to conduct or operate day-to-day business activities in a secure manner. For instance, password management and confidential information security apply to individual employees.
Personnel Management
Physical security
Hardware and Software
Policy Classification
It directs the administrator what type of technology to use and how network control should be configured and applied to the system and network administrators.
Hardware and Software
Physical security
Personnel Management
Policy Classification
Ensures compliance with the principle and practices dictated by the company because policy procedure does not work if they are violated.
Policy Enforcement
Policy Classification
Policy Audit
Policy Awareness
Security documents are living documents. It needs to be updated at specific intervals in response to changing business and customer requirements.
Policy Audit
Policy Classification
Policy Enforcement
Policy Awareness
Company employees are often perceived as a "soft" target to be compromised because they are the least predictable and easiest to exploit. Trusted employees either "disgruntle" or become framed to provide valuable information about a company.
Policy Awareness
Policy Enforcement
Policy Classification
Policy Audit
These should integrate communication and reminders to employees about what they should and shouldn't reveal information to the outsiders.
Policy Awareness
Policy Enforcement
Policy Classification
Policy Audit
(Find right ans) Process Management, There are eight (8) security processes to protect and manage data:
Privileged Password Management
This process seeks to protect the most sensitive data. Within a large organization, which has requirements to keep customer or client data secure, there is often a limited number of people who have access to the data.
Privileged Password Management
Network Administrator Daily Tasks
Network Security Audit Checklist
Firewall Audit Checklist
This checklist aims to list a series of key daily tasks performed by network administrators and provide space for those tasks to be recorded.
Network Administrator Daily Tasks
Privileged Password Management
Network Security Audit Checklist
Firewall Audit Checklist
Deals with hardware and software, training, and procedures. The risks of a system often down to both human and technical errors and particularly when both errors meet.
Network Security Audit Checklist
Firewall Audit Checklist
Privileged Password Management
Network Administrator Daily Tasks
This process is thorough and covers a series of precautions. In every step, documenting activities is encouraged.
Firewall Audit Checklist
Network Security Audit Checklist
Privileged Password Management
Network Administrator Daily Tasks
Is set up on a staff member's laptop, which allows the staff member to connect to the office network remotely.
Virtual Private Network (VPN) Configuration
Apache Server Setup
E-mail Server Security
Penetration Testing
The most popular server in the world. It caters different methods of setup by walking through alternative commands.
Apache Server Setup
Virtual Private Network (VPN) Configuration
E-mail Server Security
Penetration Testing
One of the first ways anyone is going to try to get into a company. Fighting off phishing attacks and other malicious attempts to compromise security relies on both strong technical resilience and a high level of professional training.
E-mail Server Security
Virtual Private Network (VPN) Configuration
Apache Server Setup
Penetration Testing
This involves testing systems security by trying to break into it. It is centered around trying to find vulnerabilities in a system and then attempting to sneak inside.
Penetration Testing
E-mail Server Security
Virtual Private Network (VPN) Configuration
Apache Server Setup
Enables the identification and correction of trends that could lead to business problems such as network instability and service interruption.
Network compliance
Network Security Audit Checklist
Network Administrator Daily Tasks
Network setup
Is the science of secret writing to keep the data secret and an important aspect when dealing with network security.
Cryptography
Cyber Interactions
Network compliance
Network setup
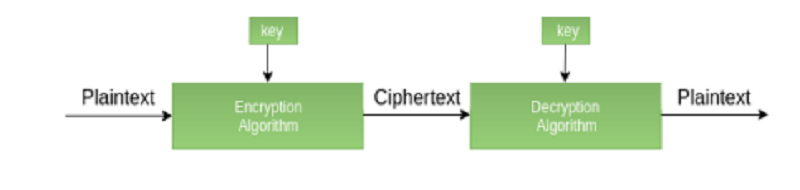
It involves usage of one (1) secret key along with encryption and decryption algorithms which help in securing the contents of the message.
Symmetric key cryptography
Asymmetric key cryptography
Hashing
Cryptanalysis
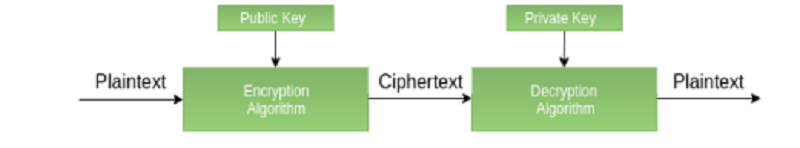
Also known as "public key cryptography," it involves the usage of a public key along with the secret key. It solves the problem of key distribution as both parties use different keys for encryption or decryption.
Asymmetric key cryptography
Symmetric key cryptography
Hashing
Cryptanalysis
It involves taking the plain-text and converting it, This process ensures the integrity of the message
Hashing
Cryptanalysis
Asymmetric key cryptography
Symmetric key cryptography
Is the study of cipher text, and ciphers to understand how they work as well as find and improve techniques for defeating or weakening threats.
Cryptanalysis
Hashing
Asymmetric key cryptography
Symmetric key cryptography
(Find wrong ans) 3 Types of Attacks in Cryptanalysis:
Classical Attack
Social Engineering Attack
Implementation Attacks
Direct Attack
It can be divided into mathematical analysis and brute force attacks. Brute force attacks run the encryption algorithm for all possible cases of the keys until these find a match. The encryption algorithm is treated as a black box.
Classical Attack
Social Engineering Attack
Implementation Attacks
Direct Attack
It is something dependent on the human factor. Tricking someone into revealing their passwords to the attacker or allowing access to the restricted area comes under this attack. People should be cautious when revealing their passwords to any third party that is not trusted.
Social Engineering Attack
Classical Attack
Implementation Attacks
Direct Attack
A side-channel analysis can be used to obtain a secret key for this kind of attack. They are relevant in cases where the attacker can obtain physical access to the cryptosystem.
Implementation Attacks
Social Engineering Attack
Classical Attack
Analytical attacks
Are those attacks which focus on breaking the cryptosystem by analyzing the internal structure of the encryption algorithm.
Analytical attacks
Classical Attack
Implementation Attacks
Direct Attack
(Find wrong ans) Classical Encryption Techniques
Caesar Cipher
Keyword Ciphers
Giovanni's Method
Transposition Techniques
Polyalphabetic Ciphers
Crypto Method
It is one of the earliest known and simplest ciphers. It is a type of substitution cipher in which each letter in the plaintext is shifted to a certain number of places down the alphabet.
Caesar Cipher
Keyword Ciphers
Giovanni's Method
Transposition Techniques
To use this method for constructing the ciphertext alphabet, pick a keyword and write it down while ignoring the repeated letters. Follow it with the letters of the alphabet that have not yet been used.
Keyword Ciphers
Caesar Cipher
Polyalphabetic Ciphers
Transposition Techniques
Suggested that one can also pick a keyletter and begin the keyword UNDER that letter of the plaintext.
Giovanni's Method
Caesar Cipher
Polyalphabetic Ciphers
Transposition Techniques
Is archived by performing some permutation on the plaintext letters. The simplest such cipher is the rail fence technique, in which the plaintext is written down as a sequence of diagonals and then read off as a sequence of rows.
Transposition Techniques
Polyalphabetic Ciphers
Giovanni's Method
Keyword Ciphers
Another way to improve on the simple monoalphabetic techniques is to use different monoalphabetic substitutions as on proceeds through the plaintext message. The best-known and the simplest algorithm is referred to as the Vigenere cipher.
Polyalphabetic Ciphers
Transposition Techniques
Giovanni's Method
Keyword Ciphers
{"name":"Cybersec (04 handout 1 and 2 Security systems engineering )", "url":"https://www.quiz-maker.com/QPREVIEW","txt":"It is the statement of responsible decision makers about the protection mechanism of a company's crucial, physical, and information assets., does not specify a technological solution. Instead, it specifies sets of intentions and conditions that will aid in protecting assets along with its proficiency to organize a business., Security policy development is a joint or collective operation of all entity of an organization that is affected by its rules.","img":"https://www.quiz-maker.com/3012/CDN/95-4639690/policy.png?sz=1200"}